2.5.1 镜像官网搜索 elasticsearch
2.5.2 直接拉取镜像:
sudo docker pull elasticsearch:7.4.22.5.3 安装es容器
2.5.3.1 创建所需目录:
mkdir -p /mydata/elasticsearch/config/
mkdir -p /mydata/elasticsearch/data/
echo "http.host: 0.0.0.0">>/mydata/elasticsearch/config/elasticsearch.yml2.5.3.2 创建实例并启动:
elasticsearch:
sudo docker run --name elasticsearch -p 9200:9200 -p 9300:9300 \
-e ES_JAVA_OPS="-Xms256m -Xmx256m" \
-v /mydata/elasticsearch/config/elasticsearch.yml:/usr/share/elasticsearch/config/elasticsearch.yml \
-v /mydata/elasticsearch/data:/usr/share/elasticsearch/data \
-v /mydata/elasticsearch/plugins:/usr/share/elasticsearch/plugins \
-d elasticsearch:7.4.2注意:
chmod -R 777 /mydata/elasticsearch
要有访问权限
参数说明:
-p 9200:9200 将容器的9200端口映射到主机的9200端口;
–name elasticsearch 给当前启动的容器取名叫 elasticsearch
-v /mydata/elasticsearch/data:/usr/share/elasticsearch/data 将数据文件夹挂载到主机;
-v /mydata/elasticsearch/config/elasticsearch.yml:/usr/share/elasticsearch/config/elasticsearch.yml 将配置文件挂载到主机;
-d 以后台方式运行(daemon)
-e ES_JAVA_OPS=”-Xms256m -Xmx256m” 测试时限定内存小一点
2.5.3.3 启动elasticsearch容器
docker start elasticsearch2.5.4 访问elasticsearch
2.5.5 问题小结
如果遇到已有容器的冲突, 需要删掉原来的:
docker: Error response from daemon: Conflict. The container name "/elasticsearch" is already in use by container "1a2e7069114ede501f687e3435b76fbc546061959b773f51681d10008bab4342". You have to remove (or rename) that container to be able to reuse that name.解决方式: docker ps -a列出所有, 删掉之前的镜像:
[root@localhost conf]# docker ps -a
CONTAINER ID IMAGE CREATED STATUS PORTS NAMES
1a2e7069114e elasticsearch:7.4.2 9 minutes ago Exited (143) About a minute ago 0.0.0.0:9200->9200/tcp, 0.0.0.0:9300->9300/tcp elasticsearch
[root@localhost conf]# docker rm 1a2e7069114e
1a2e7069114e
[root@localhost conf]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES2.5.6 配置xpack安全认证
然后
- 调整elasticsearch.yml配置:
# 可以任意节点访问
http.host: 0.0.0.0
# 单节点es
discovery.type: single-node
# 配置可以跨域访问: cors
http.cors.enabled: true
http.cors.allow-origin: "*"
# xpack 配置通信证书
xpack.security.enabled: true
#xpack.security.transport.ssl.enabled: true
#xpack.security.transport.ssl.verification_mode: certificate
#xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
#xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
将容器内部config拷贝到宿主机目录(这一步也可以忽略):
如果遇到文件访问不到的问题, 可以先在 docker run 时去掉配置, 启动后再加入, 然后 restart;# 将容器内部config拷贝到宿主机目录: docker cp 83c34a872f4c:/usr/share/elasticsearch/config/ .借助elasticsearch-certutil命令生成证书:
# 进入容器 docker exec -it elasticsearch bash # 生成证书 bin/elasticsearch-certutil cert -out config/elastic-certificates.p12 -pass ""此时目录下会多出2个文件:elastic-certificates.p12 和 elasticsearch.keystore
配置通信证书: 最后部分
# 可以任意节点访问
http.host: 0.0.0.0
# 单节点es
discovery.type: single-node
# 配置可以跨域访问: cors
http.cors.enabled: true
http.cors.allow-origin: "*"
# xpack 配置通信证书
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
设置密码: 我们用
interactive的部分, 比如设置123456需要连续输入6组(如果都用相同密码,得12次);需要配上
xpack.security.enabled: true先重启一次才能执行下面命令
bin/elasticsearch-setup-passwords interactive --手动配置每个用户密码模式
# bin/elasticsearch-setup-passwords auto --自动配置每个用户密码模式然后访问9200就可以看到登录页面了:
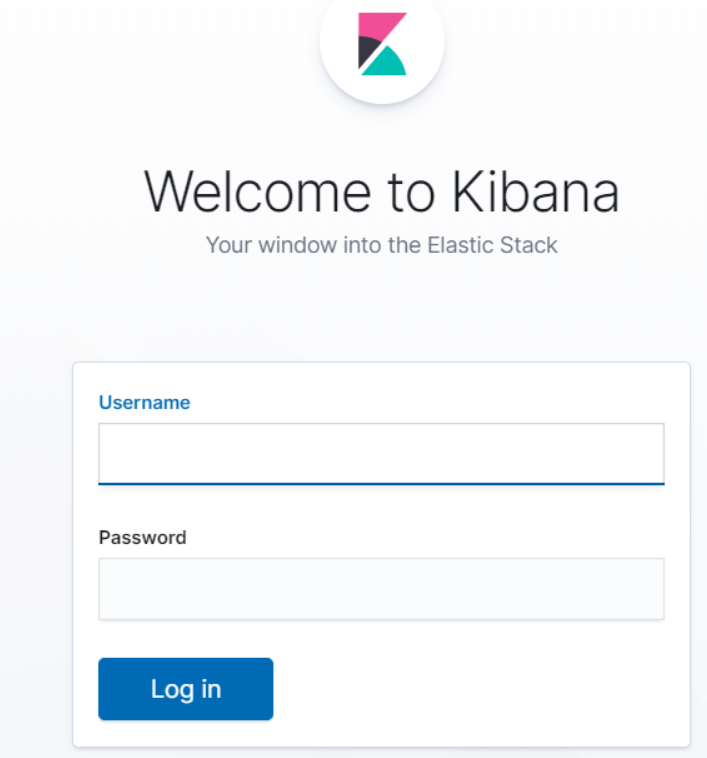
kibana也设置权限: 需要 进入kibana容器中在 kibana.yml中增加在es里设置的用户名和密码, 可以用”elastic”的密码
elasticsearch.username: "elastic" elasticsearch.password: "123456"访问5601端口, 就能看到登录页面了. 如果不配置用户名密码, 就会出现下面一坨错误的:
如果不添加用户名和密码, docker logs kibana会看到一堆错误日志:
{"type":"log","@timestamp":"2020-08-18T17:32:41Z","tags":["reporting","esqueue","queue-worker","error"],"pid":6,"message":"ke085hyf00065225910v4sk6 - job querying failed: [security_exception] missing authentication credentials for REST request [/.reporting-*/_search], with { header={ WWW-Authenticate=\"Basic realm=\\\"security\\\" charset=\\\"UTF-8\\\"\" } } :: {\"path\":\"/.reporting-*/_search\",\"query\":{},\"body\":\"{\\\"seq_no_primary_term\\\":true,\\\"_source\\\":{\\\"excludes\\\":[\\\"output.content\\\"]},\\\"query\\\":{\\\"bool\\\":{\\\"filter\\\":{\\\"bool\\\":{\\\"minimum_should_match\\\":1,\\\"should\\\":[{\\\"term\\\":{\\\"status\\\":\\\"pending\\\"}},{\\\"bool\\\":{\\\"must\\\":[{\\\"term\\\":{\\\"status\\\":\\\"processing\\\"}},{\\\"range\\\":{\\\"process_expiration\\\":{\\\"lte\\\":\\\"2020-08-18T17:32:41.117Z\\\"}}}]}}]}}}},\\\"sort\\\":[{\\\"priority\\\":{\\\"order\\\":\\\"asc\\\"}},{\\\"created_at\\\":{\\\"order\\\":\\\"asc\\\"}}],\\\"size\\\":10}\",\"statusCode\":401,\"response\":\"{\\\"error\\\":{\\\"root_cause\\\":[{\\\"type\\\":\\\"security_exception\\\",\\\"reason\\\":\\\"missing authentication credentials for REST request [/.reporting-*/_search]\\\",\\\"header\\\":{\\\"WWW-Authenticate\\\":\\\"Basic realm=\\\\\\\"security\\\\\\\" charset=\\\\\\\"UTF-8\\\\\\\"\\\"}}],\\\"type\\\":\\\"security_exception\\\",\\\"reason\\\":\\\"missing authentication credentials for REST request [/.reporting-*/_search]\\\",\\\"header\\\":{\\\"WWW-Authenticate\\\":\\\"Basic realm=\\\\\\\"security\\\\\\\" charset=\\\\\\\"UTF-8\\\\\\\"\\\"}},\\\"status\\\":401}\",\"wwwAuthenticateDirective\":\"Basic realm=\\\"security\\\" charset=\\\"UTF-8\\\"\"}\n at respond (/usr/share/kibana/node_modules/elasticsearch/src/lib/transport.js:349:15)\n at checkRespForFailure (/usr/share/kibana/node_modules/elasticsearch/src/lib/transport.js:306:7)\n at HttpConnector.<anonymous> (/usr/share/kibana/node_modules/elasticsearch/src/lib/connectors/http.js:173:7)\n at IncomingMessage.wrapper (/usr/share/kibana/node_modules/elasticsearch/node_modules/lodash/lodash.js:4929:19)\n at IncomingMessage.emit (events.js:194:15)\n at endReadableNT (_stream_readable.js:1103:12)\n at process._tickCallback (internal/process/next_tick.js:63:19)"}
{"type":"log","@timestamp":"2020-08-18T17:33:05Z","tags":["license","warning","xpack"],"pid":6,"message":"License information from the X-Pack plugin could not be obtained from Elasticsearch for the [data] cluster. [security_exception] missing authentication credentials for REST request [/_xpack], with { header={ WWW-Authenticate=\"Basic realm=\\\"security\\\" charset=\\\"UTF-8\\\"\" } } :: {\"path\":\"/_xpack\",\"statusCode\":401,\"response\":\"{\\\"error\\\":{\\\"root_cause\\\":[{\\\"type\\\":\\\"security_exception\\\",\\\"reason\\\":\\\"missing authentication credentials for REST request [/_xpack]\\\",\\\"header\\\":{\\\"WWW-Authenticate\\\":\\\"Basic realm=\\\\\\\"security\\\\\\\" charset=\\\\\\\"UTF-8\\\\\\\"\\\"}}],\\\"type\\\":\\\"security_exception\\\",\\\"reason\\\":\\\"missing authentication credentials for REST request [/_xpack]\\\",\\\"header\\\":{\\\"WWW-Authenticate\\\":\\\"Basic realm=\\\\\\\"security\\\\\\\" charset=\\\\\\\"UTF-8\\\\\\\"\\\"}},\\\"status\\\":401}\",\"wwwAuthenticateDirective\":\"Basic realm=\\\"security\\\" charset=\\\"UTF-8\\\"\"}"}备注: elasticsearch-head插件还是”集群健康值: 未连接“ , 然后换了 chrome head 插件, 可以访问了:
因为Chrome商店不能使用,安装插件麻烦:
可在github上下载elasticsearch-Head插件:es-head.crx
下载到本地, 直接拖拽到Chrome会不能使用,告诉你非Chrome来源的。
这个时候将文件后缀名”.crx”改为”.rar”,然后解压到文件夹里,再通过Chrome“加载已解压的扩展程序”按钮加入文件夹就可以使用了。
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至 hi@niewj.com